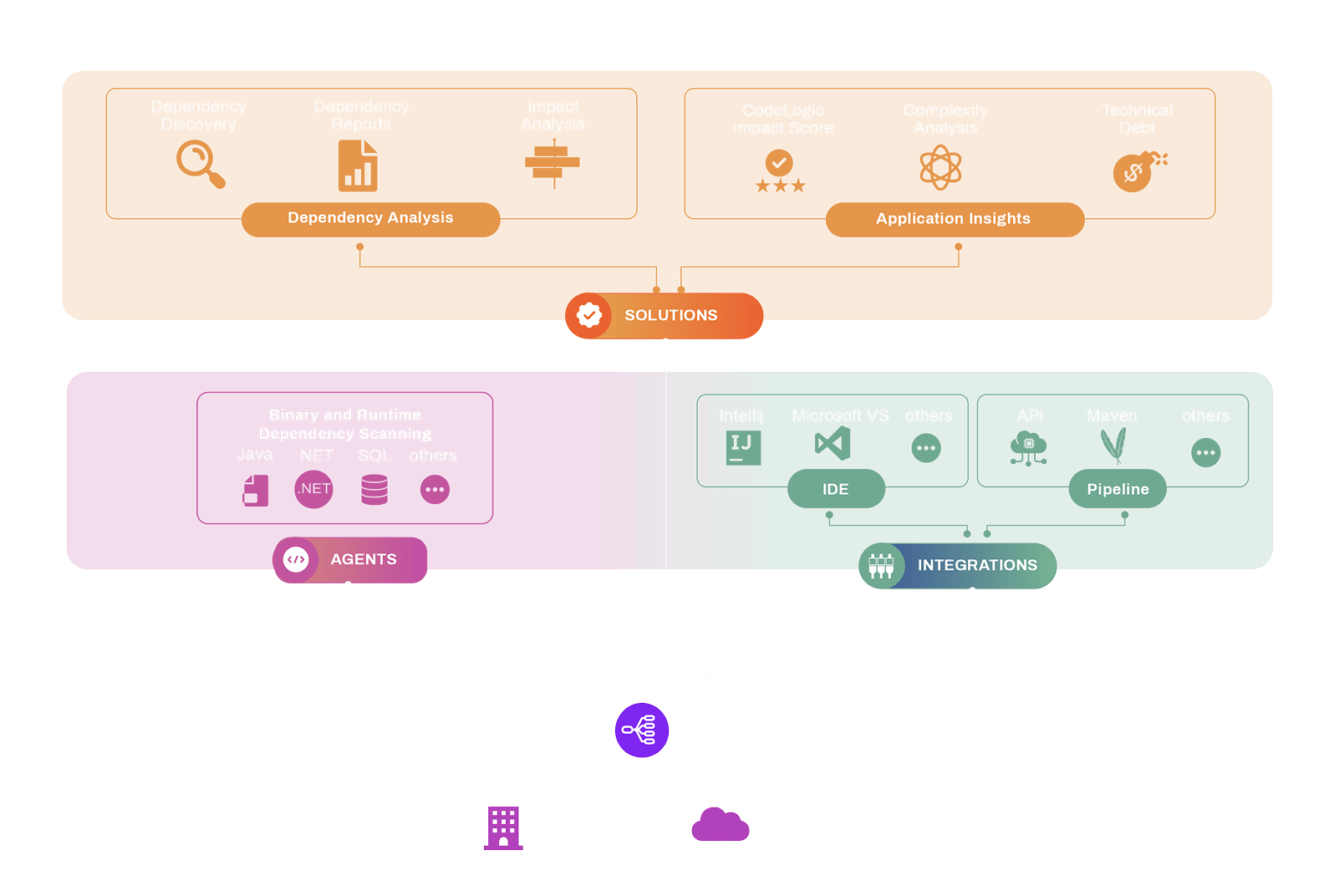
How CodeLogic Works
A True Software Intelligence Platform
CodeLogic is a true Software Intelligence Platform that builds a comprehensive dependency database using both static and runtime inspection, enabling you to do database and data model inspection and stored procedure decomposition with full reporting and is extensible via APIs.
- Comprehensive Dependency Database
- Static & Runtime inspection
- Database & Data model inspection
- Stored Procedure decomposition
- Reporting
- Extensible via API’s
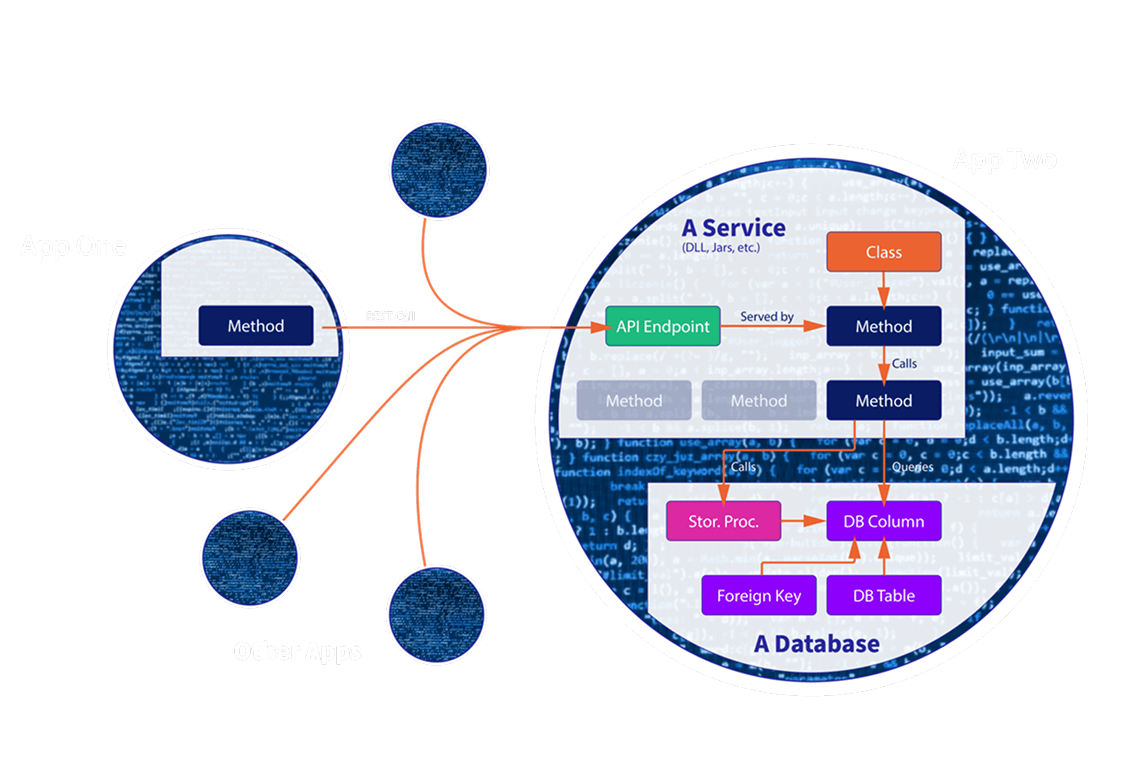
CodeLogic Digs Deep
Binary Artifact Decomposition
- Analyzes bytecode, IL, and source based on language requirements
- Establishes baseline dependency and relationship data
Runtime inspection
- Observes runtime behavior to gather dependencies data that manifests at execution
Database / Data Model Scanning
- Performs schema discovery and identifies common ORM relationships
- Decomposes and analyzes code and stored procedures, functions, packages, and triggers on the server side
Code Fearlessly
CodeLogic allows you to Code Fearlessly, so you can:
Impact Assessment: Use CodeLogic to plan ticket scope for a sprint
- Quickly assess the breadth and depth of a component's dependencies during task / ticket planning
- Reduce “points guessing”
Release Assistant: Use CodeLogic to plan a major change
- See touchpoints and changes for version upgrades to libraries and frameworks
- Understand major impacts between versions of software and components releases
CodeLogic augmented AI: Automatically receive interactive guidance (coming April 2025)
- Let generative AI interactively analyze dependencies, relationships, complexity, and architecture
- Provides continuous knowledge graph data to guide AI driven development
IDE Plugin: Understand complex dependencies impact during development
- Before, or while modifying code, check to see impact within projects and across API and project boundaries
CodeLogic Annotations: protect critical sections of code, or note test impacts
- Attribute ownership and enable annotation driven notifications via instant messaging
Change Requests: Use CodeLogic to review differential impact for inbound code
- See Red-Green data in graph form to understand scope and impact of inbound codebase changes
CodeLogic Annotations: receive alerts on annotation hits via IM during change requests
- Receive impact notifications based on dependency “hits” flagged by annotations
- Understand if something afield is about to impact (or be impacted by) proposed changes
- Understand what tests are impacted by changes and need reevaluation by test teams
- Can be used to implement informal governance model (will be formalized in the future)
Change Requests and Release Assistant: Use CodeLogic to review post-build issues
- Review recent changes via differential graphs to understand where a dependency impact may have originated
- Understand where to retrofit code with annotations
Annotations + API integrations: Use CodeLogic to halt a build or deployment
- Create custom consumption of annotation-based alerting through API integrations
- CodeLogic API is fully published and open
- CodeLogic agent infrastructure is plugin extensible

Enterprise-scale software systems have become so complex that they are difficult to maintain, expensive to modify, susceptible to security risks, and prone to breakage. In many cases, the depth, breadth, and degree of interconnectedness within modern enterprise-scale software systems defies human understanding.




